Cointelegraph Front-End Exploit: Phishing Airdrop Scam Targets Users
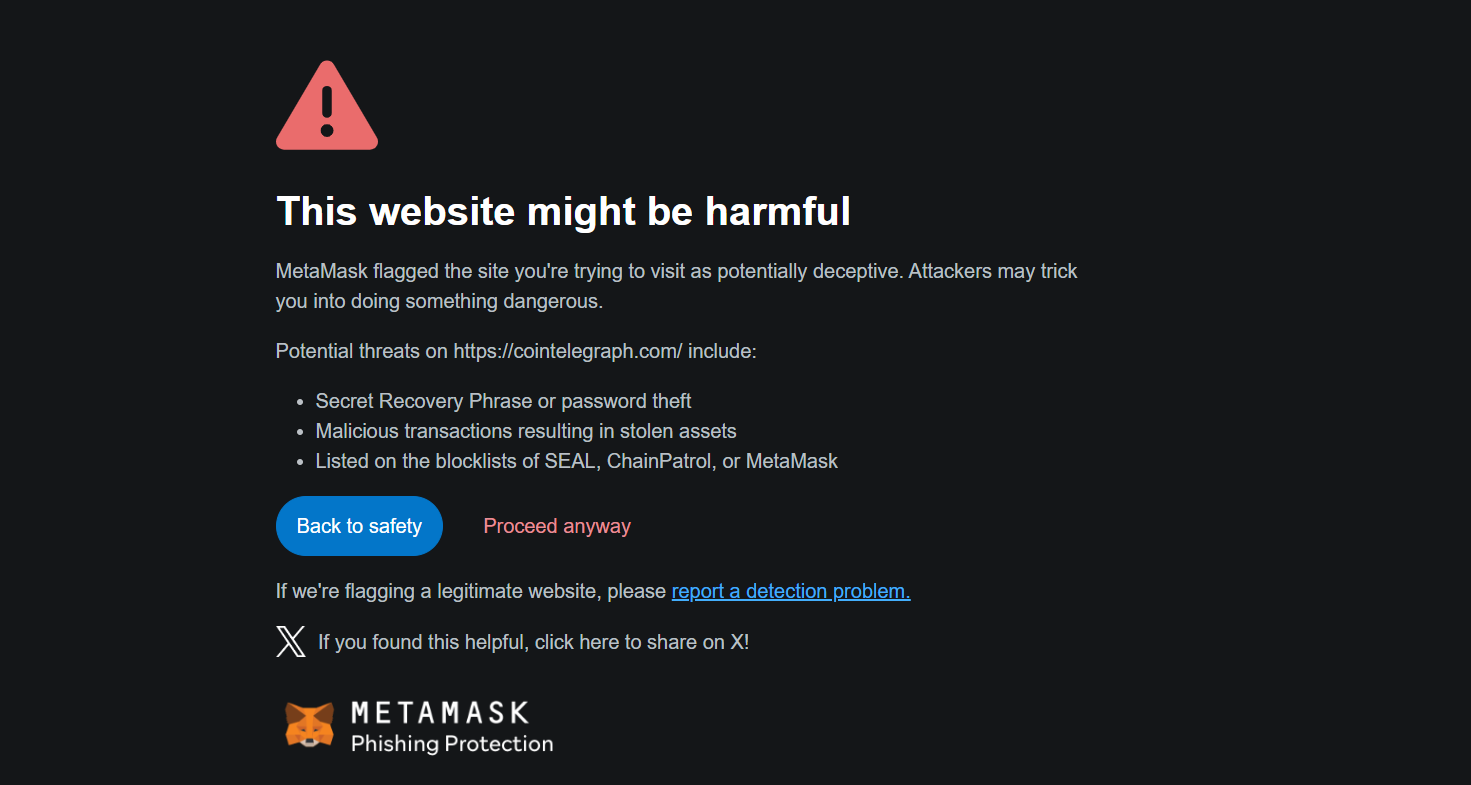
Cointelegraph Website Breach: Fake airdrop Scams Emerge
Overview of the Incident
Recently, Cointelegraph’s website experienced a security breach that compromised its front-end. This vulnerability allowed malicious actors to introduce deceptive pop-up notifications.
Details of the Malicious Activity
Fake airdrop Offers
Users visiting the compromised site were confronted with fraudulent advertisements promoting non-existent ‘CoinTelegraph ICO Airdrops.’ These scams aimed to lure unsuspecting visitors into providing sensitive information or making investments.
Impact on Users
The breach raised significant concerns among the cryptocurrency community, as many users rely on Cointelegraph for accurate and trustworthy information. The presence of such scams could lead to financial losses and erode user trust in the platform.
Response from Cointelegraph
Security Measures Implemented
In response to the incident, Cointelegraph has initiated a thorough investigation to identify the source of the exploit. The team is also implementing enhanced security protocols to prevent future breaches.
User Advisory
Cointelegraph has urged its audience to remain vigilant and exercise caution when encountering pop-ups or offers that seem suspicious. Users are encouraged to verify information through official channels before engaging with any promotional content.
Conclusion
The recent compromise of Cointelegraph’s website highlights the ongoing risks associated with online security in the cryptocurrency sector. As the platform works to rectify the situation, users are reminded to stay informed and cautious against potential scams.







